As organizations increasingly turn to cloud systems to manage vast amounts of data in today’s world, it is essential to know what are the security risks of cloud computing. Despite the significant amount spent on cloud services, businesses must remain aware of the security risks related to this emerging technology. With forecasts stating that the global public cloud market will reach $623.3 billion by 2023, now is more important than ever for organizations to understand these threats and take proactive measures for protecting sensitive information.
Read also: Types of Cloud Computing
What Are The Security Risks Of Cloud Computing?
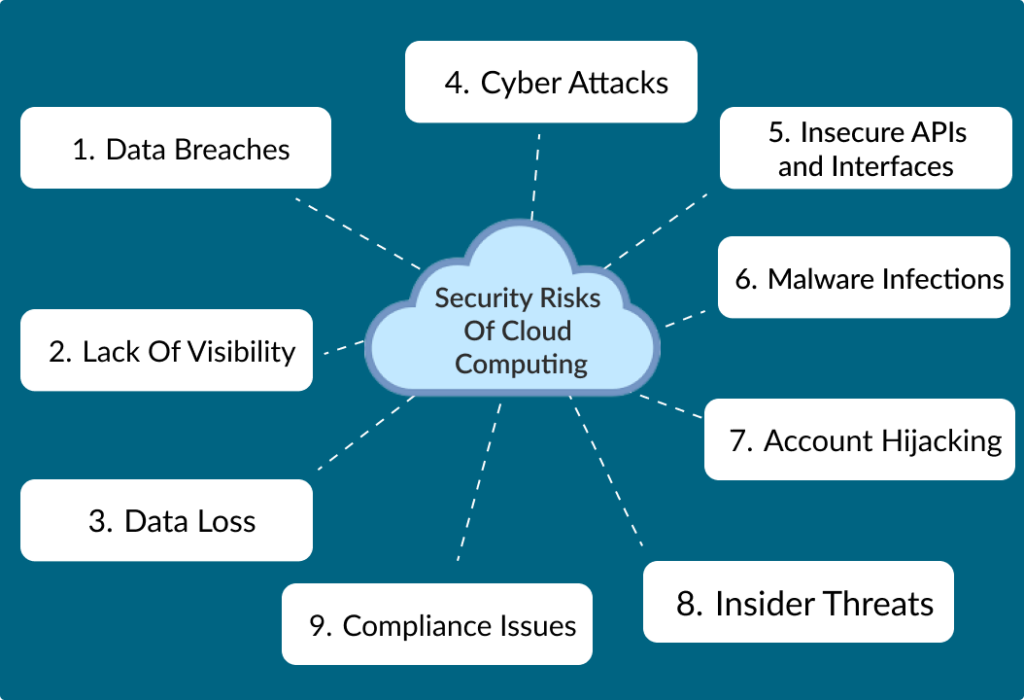
Cloud computing services are used by many organizations and businesses and it provides many advantages. From scalability to cost-effectiveness and reliability, cloud storage provides the best services. However, we need to consider the cons of cloud computing as well. Several risks are attached to cloud computing which is as follows:
Data Breaches
A data breach is defined as when a company’s personal and sensitive data is exposed to a third party with unauthorized access. Cloud services store large amounts of data and in case a breach happens it can lead to significant amounts of data loss and unwanted data access to the third party.
This can happen by a variety of methods and vulnerabilities to cloud infrastructure are one of them. Human error mistakes can also be made, however, the result can cause serious consequences.
Lack Of Visibility
When you shift data from one source to another, you also transfer the security risks of the cloud. Responsibility is transferred from the in-house team to the cloud service provider. This results in a loss of visibility into some network operations. In case the user doesn’t know what he is doing or doesn’t have any idea then it can lead to issues regarding the resources. This results in service usage and cost.
Data Loss
A survey was done in which about 64% of the respondents reported that their biggest concern regarding cloud computing was data loss. This is also known as data leakage. When an organization shifts its data to cloud computing services, vulnerabilities are also increased. Your data can be corrupted, deleted, or become unreadable to the users.
This could be due to many reasons like issues in your hardware or software or your system being updated properly. However, this is a concern for your data security. Sensitive data could fall into the wrong hands which could be harmful to the organization.
Cyber Attacks
Hackers attempting to hack your personal data and misuse it have increased. These attacks have become significant for cloud computing. Although cloud services have strong security measures hackers still somehow access your data.These cyber-attacks can result in the loss of sensitive data, the compromise of user credentials, and even financial loss. Many users have experienced account blockage due to cyber attacks.
Insecure APIs and Interfaces
Now you might have an overview about what are the security risks of cloud computing. Another risk is Insecure APIs and Interfaces. Cloud service providers offer the service of interfaces and application programming interfaces (APIs). These services are used to manage the resources of cloud computing.
Although these services are highly secured and protected these tools are still vulnerable to attacks. Organizations need to step up their game to prevent such issues. If attackers are able to exploit these services then sensitive data can be misused.
Malware Infections
Malware infections are one of the major security concerns of cloud computing. These infections result in disrupted business operations, and loss of security controls and also affects the systems that are connected to the infectious device. About 90% of organizations face this issue when moving their data.
Malware is basically software that is solely designed for the purpose of getting unauthorized access to steal information. This software disrupts and damages the data. Attackers tend to identify vulnerabilities in the Cloud software and then inject malware infection into the system. Some of the common ways through which malware function can occur are as follows:
- Web-based attacks
- Email attachments and links
- Unauthorized or vulnerable software
- File sharing
Account Hijacking
Account hijacking occurs when an attacker gains unauthorized access to a user’s account and accesses personal information. This is a serious risk in cloud computing services. Account hijacking can occur in a variety of ways including phishing attacks.
Along with this if a user gets tricked into giving their credentials and login passwords, their system can be hijacked. Weak passwords that can be easily accessed by attackers and issues or weak security of cloud computing providers are also a reason. After accessing your account, the attacker can easily manipulate your personal data the way he wants.
Insider Threats
Insider threats are another issue of cloud computing. This refers to the misuse of sensitive data by an employee of the company. Insider threats happen when an unloyal employee misuses the access they have and leaks information regarding the company.
This results in the favor of competitors. They can get access to the information that could lead them to success. Basically, these are intentionally done by a person but in some cases, these can be unintentional. Like if an employee mistakenly leaks the company’s data.
Compliance Issues
Cloud services have become common these days. No organization can thrive without cloud computing. As with the increase of data, the responsibility of managing is also increasing. More organizations are shifting their data to cloud services. But with this, they have to deal with compliance and regulatory issues as well.
Organizations and businesses need to follow the relevant laws and regulations and remain within industry standards. And in case any organizations fail to follow its obligations it would have to deal with legal and financial penalties. The company’s reputation is also disturbed because of this.
How To Tackle Security Risks Of Cloud Computing?
Now you know what are the security risks of cloud computing. The next thing is how to tackle them. Following are some of the security measures users can take to prevent unauthorized access control:
- Users need to implement strong authentication and access control measures. This will prevent unauthorized access.
- Cloud users should encrypt their sensitive data before uploading it to the cloud.
- Users need to regularly backup their data to prevent data loss in case of a security breach.
- Implement security monitoring and logging to detect and respond to security incidents in a timely manner.
- Service providers should also offer backup and disaster recovery services to their users.
- Cloud service providers should regularly update their software and security patches to fix vulnerabilities and prevent attacks.
- By conducting regular security audits and assessments users can identify security risks and vulnerabilities.
Conclusion
To wrap up, now you have an idea about what are the security risks of cloud computing. Cloud computing services are undoubtedly popular these days. For data management and security cloud, computing is an easy and accessible way. Organizations and businesses have to rely on these tools to survive.
But where every item has its pros, it has its cons as well. Users need to consider the security risks that are affiliated with cloud computing and take necessary risk assessments. Remember before signing for a service provider consider all the features as well as the security concerns. Only then make a decision.
Frequently asked Questions (FAQs)
Q No.1 What are the security risks of cloud computing?
Answer: Here are some common security risks associated with cloud computing:
- Data breaches
- Data loss
- Account hijacking
- Insecure APIs
- Insider threats
- Compliance and legal issues
Q No.2 What is cloud security with an example?
Answer: Cloud security refers to the set of practices, technologies, and policies designed to protect cloud computing environments and the data stored within them.
Example:
An example of cloud security is the use of encryption to protect data stored in the cloud. Only authorized parties with the encryption keys can decrypt and access the data.
Q No.3 What kind of security is in cloud computing?
Answer: Here are some key security mechanisms in cloud computing:
- Data Encryption
- Access Controls
- Firewalls and Network Security
- Intrusion Detection and Prevention Systems (IDPS)
- Security Monitoring and Logging
- Regular Audits and Assessments
- Physical Security
Q No.4 How do you secure cloud computing?
Answer: Securing cloud computing involves implementing a combination of measures to protect the cloud infrastructure, data, and applications. Select a reliable cloud service provider that has a strong track record in security.
Q No.5 What are cloud security controls?
Answer: Cloud security controls are a set of measures, policies, and technologies implemented to safeguard cloud environments and protect the confidentiality, integrity, and availability of data.
Q No.6 What are the 7 types of cyber security?
Answer: There are seven main types of cybersecurity
- Network Security
- Application Security
- Endpoint Security
- Data Security
- Identity and Access Management (IAM)
- Cloud Security
- Security Operations Center (SOC)
Q No.7 Does the cloud have security?
Answer: Yes, cloud computing incorporates various security measures to protect data.
Q No.8 What are the three 3 threats to information security?
Answer: The three primary threats to information security are:
- Cyberattacks encompass a wide range of malicious activities conducted by individuals or groups with the intent to compromise information systems.
- Data breaches occur when sensitive or confidential information is accessed, disclosed, or stolen by unauthorized individuals.
- Human error represents a significant threat to information security. It includes mistakes made by employees.
Q No.9 What are security attacks?
Answer: Security attacks refer to deliberate, malicious activities or actions taken with the intention of compromising the confidentiality of data.
Q No.10 What is security issue vs risk?
Answer:
Security Issue: A security issue refers to a vulnerability in a system or application that could potentially be exploited by an attacker.
Risk: Risk is the potential for harm, loss, or damage that can arise from a security issue. It assesses the likelihood of a security issue being exploited and the impact it could have on an organization.
See more